Cybersecurity researchers have flagged a new ransomware family named Ymir, which was deployed in an attack just two days after systems were initially compromised by malware called RustyStealer.
Kaspersky, the Russian cybersecurity vendor, stated, “Ymir ransomware introduces a unique combination of technical features and tactics that enhance its effectiveness. Threat actors leveraged an unconventional blend of memory management functions – malloc, memmove, and memcmp – to execute malicious code directly in memory. This approach deviates from the typical sequential execution flow seen in widespread ransomware types, enhancing its stealth capabilities.”
Kaspersky observed this ransomware in a cyber attack targeting an unnamed organization in Colombia. Initially, the RustyStealer malware was used to gather corporate credentials, which were then leveraged to gain unauthorized access to the company’s network and deploy the ransomware. The typical hand-off between an initial access broker and the ransomware crew remains unclear in this instance.
Cristian Souza, Kaspersky researcher, remarked, “If the brokers are indeed the same actors who deployed the ransomware, this could signal a new trend, creating additional hijacking options without relying on traditional Ransomware-as-a-Service (RaaS) groups.”
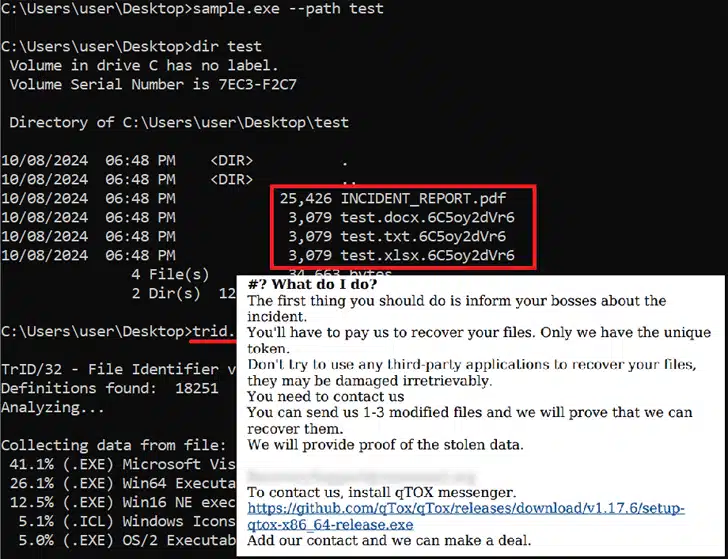
The attack installed tools like Advanced IP Scanner and Process Hacker, as well as two scripts from the SystemBC malware, setting up a covert channel for exfiltrating files. The ransomware binary uses the ChaCha20 stream cipher algorithm to encrypt files, appending the extension “.6C5oy2dVr6”.
Kaspersky noted, “Ymir is flexible: by using the --path command, attackers can specify a directory where the ransomware should search for files. If a file is on the whitelist, the ransomware will skip it and leave it unencrypted. This feature gives attackers more control over what is or isn’t encrypted.”
In related news, attackers behind the Black Basta ransomware are using Microsoft Teams chat messages and malicious QR codes to engage with prospective targets and facilitate initial access.
ReliaQuest reported, “The underlying motivation is likely to lay the groundwork for follow-up social engineering techniques, convincing users to download remote monitoring and management (RMM) tools, and gaining initial access to the targeted environment. Ultimately, the attackers’ end goal is almost certainly the deployment of ransomware.”
There are also reports of threat actors posing as IT support personnel, using Quick Assist to gain remote access, a technique highlighted by Microsoft in May 2024. As part of a vishing attack, victims are instructed to install remote desktop software like AnyDesk or launch Quick Assist.
A previous iteration of the attack used malspam tactics, inundating employees’ inboxes with thousands of emails and posing as the company’s IT help desk.
Additionally, ransomware attacks involving the Akira and Fog families have exploited systems running unpatched SonicWall SSL VPNs (CVE-2024-40766). Up to 30 new intrusions leveraging this vulnerability were detected between August and mid-October 2024, per Arctic Wolf.
These events highlight the evolving threat landscape of ransomware, despite law enforcement efforts to disrupt cybercrime groups. Last month, Secureworks noted a 30% year-over-year increase in active ransomware groups, driven by 31 new groups entering the ecosystem.
NCC Group data shows a total of 407 ransomware cases recorded in September 2024, down from 450 in August. Major sectors targeted include industrial, consumer discretionary, and information technology.
Politically motivated hacktivist groups like CyberVolk have also used ransomware as a tool for retaliation. Meanwhile, U.S. officials are seeking new ways to counter these extortion schemes, urging cyber insurance companies to stop reimbursements for ransom payments.
Anne Neuberger, U.S. Deputy National Security Adviser for Cyber and Emerging Technology, wrote in the Financial Times, “Some insurance company policies — for example covering reimbursement of ransomware payments — incentivize payment of ransoms that fuel cyber crime ecosystems. This is a troubling practice that must end.”





